User guide
C
HAPTER
3
| Windows 2000/XP Configuration
Wireless Utility Configuration
– 25 –
■
WEP – Enables the Wireless USB Adapter to use WEP shared keys.
If enabled, you must configure at least one key. Wired Equivalent
Privacy (WEP) provides a basic level of security, preventing
unauthorized access to the network and encrypting data
transmitted between wireless clients. WEP uses static shared keys
(fixed-length hexadecimal or alphanumeric strings) that are
manually distributed to all clients that want to use the network.
■
TKIP – Use Temporal Key Integrity Protocol (TKIP) keys for
encryption. WPA specifies TKIP as the data encryption method to
replace WEP. TKIP avoids the problems of WEP static keys by
dynamically changing data encryption keys.
■
AES – Use Advanced Encryption Standard (AES) keys for
encryption. WPA2 uses AES Counter-Mode encryption with Cipher
Block Chaining Message Authentication Code (CBC-MAC) for
message integrity. The AES Counter-Mode/CBCMAC Protocol (AES-
CCMP) provides extremely robust data confidentiality using a 128-
bit key. Use of AES-CCMP encryption is specified as a standard
requirement for WPA2. Before implementing WPA2 in the network,
be sure client devices are upgraded to WPA2-compliant hardware.
◆ 802.1X — Use IEEE 802.1X (802.1X) for user authentication and
distributing dynamically generated encryption keys. IEEE 802.1X is a
standard framework for network access control that uses a RADIUS
server on the local network for user authentication. The 802.1X
standard uses the Extensible Authentication Protocol (EAP) to pass user
credentials (either digital certificates, usernames and passwords, or
other) from the client to the RADIUS server.
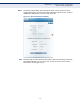
Figure 17: Profile - 802.1X Configuration
■
EAP Method (LEAP) – The Lightweight Extensible Authentication
Protocol (LEAP) is an EAP authentication type used primarily in
Cisco Aironet WLANs. It encrypts data transmissions using
dynamically generated WEP keys, and supports mutual
authentication.When LEAP is select, input LEAP identity, password,
domain name, and select encryption type. Check the Show
Password box to display password characters as you type instead of
asterisks.
■
Identity / Password – Configures the identity an password for
authentication.
■
Domain Name – Enable the wireless configuration utility to check
the end of domain name. If defects are found, the connection is
dropped.