Administrator Guide
Table Of Contents
- Dell EqualLogic Group Manager Administrator’s Guide PS Series Firmware Version 9.1 FS Series Firmware Version 4.0
- About This Manual
- About Group Manager
- Architecture Fundamentals
- Set Up the iSCSI SAN
- Post-Setup Tasks
- Data Security
- About Group-Level Security
- Enable or Disable GUI and CLI Access
- Switch Administration Authentication Type
- About Administration Accounts
- Types of Administration Accounts
- Differences Between Authentication Methods
- Administration Account Attributes
- About Security Access Protocols
- SSH Key Pair Authentication
- Minimum Requirements for Administrative Access
- Create a Local Administration Account
- Modify Local Administration Accounts
- Delete Local Administration Accounts
- About RADIUS Accounts
- About LDAP Authorization and Active Directory
- About Single Sign-On
- About SNMP Access to the Group
- About VDS and VSS Authentication
- About IPsec
- About Dedicated Management Networks
- About Volume-Level Security
- Connect Initiators to iSCSI Targets
- Access Control Methods
- About Access Policies
- Access Policies: Use Cases
- Create a New Access Policy
- Create a New Basic Access Point
- Modify or Delete a Basic Access Point
- Modify Access Policies and Basic Access Points by Volume
- Associate Access Control Policies with Volumes
- Create an Access Policy Group
- Associate an Access Policy Group to a Volume
- Manage Access Controls for VDS/VSS Access
- Authenticate Initiators with CHAP
- Display Local CHAP Accounts
- Create a Local CHAP Account
- Modify a Local CHAP Account
- Delete a Local CHAP Account
- Configure CHAP for Initiator Authentication on Existing Volumes
- Configure CHAP for Initiator Authentication on New Volumes
- Configure CHAP Accounts on a RADIUS Authentication Server
- Configure Target Authentication
- About iSNS Servers
- Prevent Discovery of Unauthorized Targets
- About Multihost Access to Targets
- About Snapshot Access Controls
- About NAS Container Security
- PS Series Group Operations
- About Group Network Configuration
- Modify the Group IP Address or Group Name
- Add a Member to an Existing Group
- Set the RAID Policy and Pool for a New Member
- Enable and Disable a Volume RAID Preference
- About Overriding Automatic Load Balancing
- Shut Down a Group
- Create an Empty Storage Pool
- Create a Storage Pool from an Existing Member
- Change a Storage Pool Name or Description
- Merge Storage Pools
- Delete a Storage Pool
- About Groupwide Volume Defaults
- About Space Borrowing
- About Compression of Snapshots and Replicas
- Compression Prerequisites
- About Rehydration
- About Compression Statistics
- Compression Statistics by Pool
- Compression Statistics by Member
- Compression Statistics by Volume
- Member Compression States
- Enable Compression
- Suspend Compression
- Resume Compression
- View Compression Statistics by Pool
- View Compression Statistics by Member
- View Compression Statistics by Volume
- Compression Commands in the CLI
- About Volumes
- Create a Volume
- Modify a Volume Name or Description
- Modify a Volume Permission
- Modify a Volume Alias
- Modify the Administrator for a Volume
- About Smart Tags
- Set a Volume Offline or Online
- Delete a Volume
- About Volume Collections
- About Volume Folders
- About Restoring Deleted Volumes
- About Changing the Reported Volume Size
- About Reclaiming Unallocated Space
- Set a Volume or Snapshot with Lost Blocks Online
- Volume and Snapshot Status
- Volume and Snapshot Requested Status
- About Managing Storage Capacity Utilization On Demand (Thin Provisioning)
- About Improving Pool Space Utilization (Template Volumes and Thin Clones)
- About Data Center Bridging
- VMware Group Access Panel
- NAS Operations
- NAS Cluster Operations
- NAS Cluster Configuration
- NAS Cluster Post-Setup Tasks
- Modify a NAS Cluster Name
- Modify NAS Clusterwide Default NAS Container Settings
- Select an NFS Protocol Version
- Modify the Size of the NAS Reserve
- Add a Local Group for a NAS Cluster
- Delete a Local Group from a NAS Cluster
- Add a Local User on a NAS Cluster
- Modify a Local User on a NAS Cluster
- Delete a Local User from a NAS Cluster
- Map Users for a NAS Cluster
- Set the User Mapping Policy for a NAS Cluster
- Delete a User Mapping for a NAS Cluster
- Configure an Active Directory for a NAS Cluster
- Configure Preferred Domain Controllers
- Leave Active Directory
- Configure or Modify NIS or LDAP for a NAS Cluster
- Delete NIS or LDAP Configuration for a NAS Cluster
- Modify the Client Network Configuration
- Configure DNS for a NAS Cluster
- About the Internal Network Required for NAS Configuration
- About NAS Cluster Maintenance Mode
- Shut Down and Restart a NAS Cluster Manually
- About Deleting a NAS Cluster
- NAS Controller Operations
- NAS Container Operations
- Create a NAS Container
- Modify NAS Clusterwide Default NAS Container Settings
- Modify NAS Clusterwide Default NAS Container Permissions
- Modify NAS Clusterwide Default NFS Export Settings
- Modify NAS Clusterwide Default SMB Share Settings
- Modify a NAS Container Name
- Modify the Size of a NAS Container
- Modify the Snapshot Reserve and Warning Limit for a NAS Container
- Modify the In-Use Space Warning Limit for a NAS Container
- Modify a NAS Container for Few Writers Workloads
- Delete a NAS Container
- NFS Netgroups
- Access NFS Exports
- Create an NFS Export
- Modify the Client Access Setting for an NFS Export
- Modify the Permission for an NFS Export
- Modify the Trusted Users for an NFS Export
- Modify NAS Clusterwide Default NFS Export Settings
- Modify an NFS Export Directory
- Modify an NFS Export
- About NFS Export Security Methods
- Delete an NFS Export
- About SMB Shares
- Access SMB Shares in Windows
- Mount a NAS SMB Share from UNIX
- Create an SMB Share
- Set the SMB Password
- Modify an SMB Share Directory
- Delete an SMB Share
- Rebalance SMB Client Connections Across NAS Controllers
- Enable or Disable SMB Message Signing
- Enable or Disable SMB Message Encryption
- Modify SMB Share NAS Antivirus Settings
- Access-Based Enumeration
- About SMB Home Shares
- Create a NAS Thin Clone
- Client Networks
- About NAS Antivirus Servers
- How NAS Antivirus Protects Data
- NAS Antivirus Server Specifications
- Add a NAS Antivirus Server
- Modify a NAS Antivirus Server
- Delete a NAS Antivirus Server
- About NAS Antivirus Clusterwide Defaults
- Enable the NAS Antivirus Service on an SMB Share
- Monitor the NAS Antivirus Service
- NAS Directory Paths and File Types Scan
- Antivirus Policy
- Access Infected Files
- Create a NAS Container Quota
- Modify a NAS Container Quota
- Delete a NAS Container Quota
- About Quota Directories
- Quotas and NAS Containers
- About NAS Thin Provisioning
- NAS Container Storage Space Terminology
- About NAS Containers
- About Data Rehydration
- NAS Container Data Reduction
- Enable Data Reduction
- Modify NAS Container Data Reduction Settings
- Modify NAS Cluster Default Data Reduction Settings
- Data Reduction Policy
- Create Default Data Reduction Properties
- About NAS Data Reduction Schedules
- FS Series VAAI Plugin
- Diagnose and Resolve NAS Cluster and PS Series Issues
- About Backing Up and Protecting Your Data
- About Volume Data Protection
- Protect NAS Container Data with NDMP
- About Snapshots
- How Snapshots Work
- About Snapshot Reserve
- Create a Snapshot
- Set a Snapshot Online or Offline
- Clone a Snapshot to Create a New Volume
- Modify a Snapshot Name or Description
- Delete Snapshots
- Restore a Volume from a Snapshot
- About Snapshots and NAS Container Data
- About Snapshot Collections
- About Snapshot Space Borrowing
- About Replication
- About Schedules
- About Data Recovery
- About Recovering Data from a Snapshot
- Failback to Primary Operation (Manual)
- Move a Failback Replica Set to a Different Pool
- Replicate to Partner Operation (Manual)
- Switch Partner Roles Permanently
- Make a Temporary Volume Available on the Secondary Group
- Replicate a Recovery Volume to the Primary Group
- Promote an Inbound Replica Set to a Recovery Volume
- How to Handle a Failed Operation
- Fail Back to the Primary Group
- Volume Failover and Failback
- Recover Data from a Replica
- About NAS Disaster Recovery
- About Cloning Volumes
- About Synchronous Replication
- How Synchronous Replication Works
- Compare SyncRep and Traditional Replication
- How Synchronous Replication Protects Volume Availability in Different Scenarios
- Requirements for Using Synchronous Replication
- Synchronous Replication States
- About System Snapshots and SyncRep
- About Synchronous Replication and Snapshots
- About Synchronous Replication Switches and Failovers
- About Synchronous Replication Volume Collections
- About Using Thin Clones and Templates with Synchronous Replication
- Configure Synchronous Replication (SyncRep) on a Volume
- Disable Synchronous Replication (SyncRep) for a Volume
- Monitor Synchronous Replication (SyncRep) Volumes
- Pause Synchronous Replication (SyncRep)
- Resume Synchronous Replication (SyncRep)
- Enable Synchronous Replication (SyncRep) for a Volume Collection
- Disable Synchronous Replication (SyncRep) for a Volume Collection
- Change the Pool Assignment of a Synchronous Replication (SyncRep) Volume
- View the Distribution of a Volume Across Pools
- About Switching and Failing Over SyncRep Pools
- Disconnect the SyncActive Volume
- About Self-Encrypting Drives (SEDs) and AutoSED
- Scenarios Covered by AutoSED
- Scenarios Not Covered by AutoSED
- About Self-Encrypting Drives (SED)
- How Self-Encryption Protects Data
- About SED Members in a Group
- Back Up a Self-Encrypting Drive (SED) Key
- Self-Encrypting Drives (SED) Frequently Asked Questions (FAQ)
- Why are my backups always different?
- Why is a secure-erase command not available?
- What is the difference between a locked drive and a securely erased drive?
- I accidentally reset an SED array. What can I do?
- What if the entire array is stolen?
- What if the grpadmin password is stolen?
- Is it safe to discard or return a locked SED?
- Can I add SEDs to a non-SED array, or vice versa?
- Does a SED system also use RAID?
- Does SED encrypt my volumes?
- If I create a new set of backup units, does the new set invalidate the previous set of backup units?
- Self-Encrypting Drives (SED) Examples
- Self-Encrypting Drives (SED) Advanced Encryption
- About Monitoring
- Tools That Monitor and Manage Storage Performance
- Monitor Group Members
- About Storage Performance
- Monitor Administrative Sessions
- Monitor Snapshot Schedules
- Monitor Volumes and Snapshots
- About Monitoring Replication
- About Monitoring Replication Operations
- Monitor Alarms and Operations
- About Diagnostics
- Troubleshooting Performance Issues
- Third-Party Copyrights
NOTE: Replication history displays the last 10 replicas only.
In addition, you should monitor the usage of delegated space. If free delegated space is not available, replica reserve cannot increase
automatically. You can also monitor replica reserve for a volume. Insucient replica reserve limits the number of replicas.
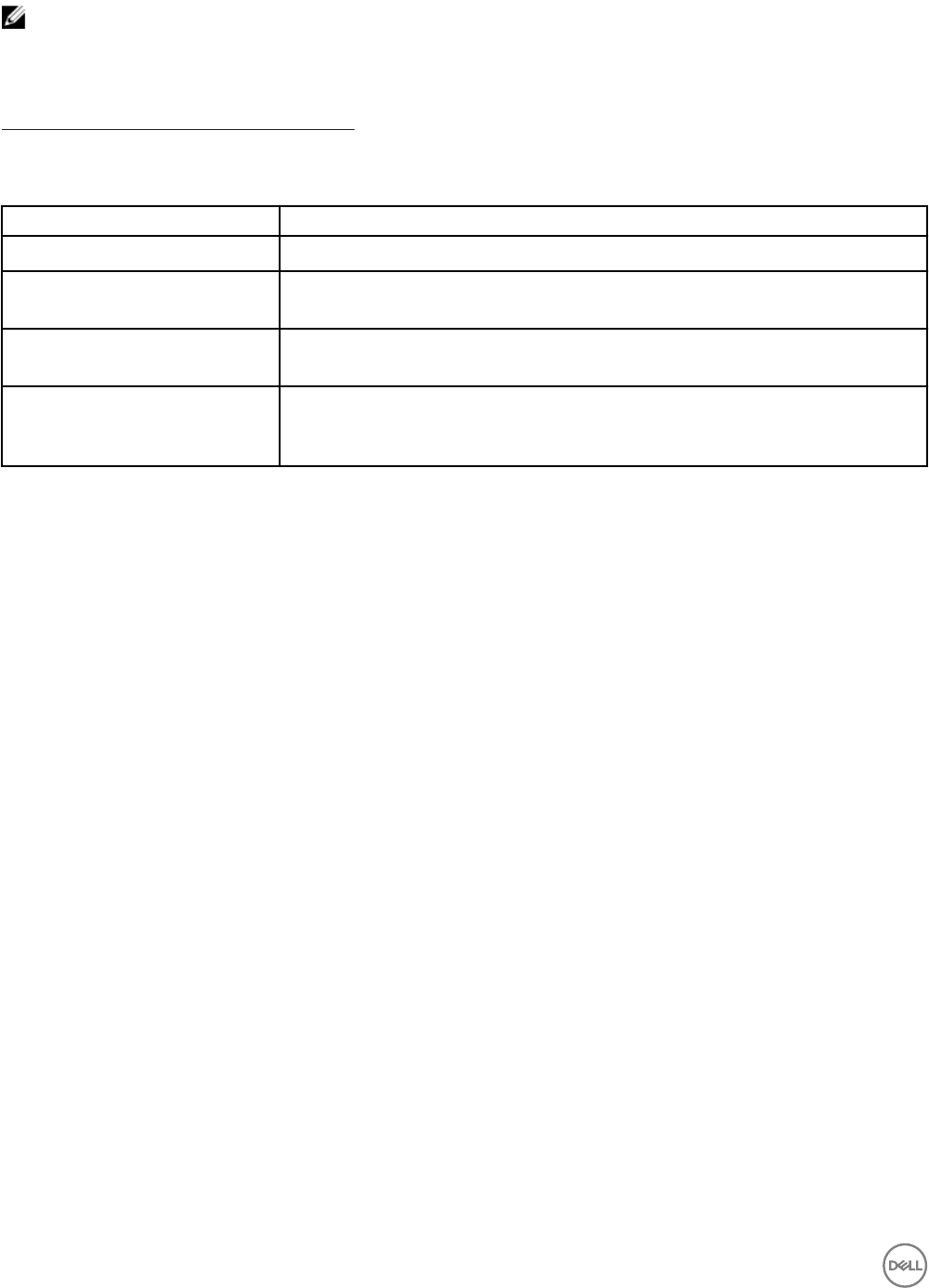
Table 63. Best Practices for Monitoring Replication suggests areas that you should monitor when performing replication between
groups, and describes best practices to avoid replication issues associated with these areas.
Table 63. Best Practices for Monitoring Replication
Issue Best practice to avoid issue
Incomplete replication operations If a replication operation fails to complete, you might need to increase replication space.
Incomplete manual transfer
operations or failback operations
Some operations require multiple tasks that administrators must complete. Make sure you
complete all multitask operations.
Low free delegated space If delegated space is low, replica reserve space might not be able to increase automatically
to store new replicas.
Number of replicas If too many replicas exist, consider decreasing the replica reserve percentage. If too few
replicas exist, consider increasing the replica reserve percentage. A low free replica reserve
can indicate optimal use of replica reserve space, if the desired number of replicas exist.
Monitoring Replication History
You should periodically monitor information about past replication operations, including volume and partner information, start time,
end time, and duration for the replication operation, and the amount and speed of data transferred.
Also, you should examine the replication-duration information. If you see long replication times, make sure the network connection
between the partners is sucient. A slow network link between the partners can cause long replication times. If a replication
operation makes no progress, the group generates a warning event. Make sure you have adequate network bandwidth between the
groups, in addition to full IP routing. If necessary, increase the network bandwidth.
Additionally, check how much data you are replicating. You might want to use manual transfer replication if you are transferring a
large amount of data.
Monitoring Replication Partners
You can monitor information about all the congured replication partners for a group. This information includes both outbound details
(volumes on this group replicating to others) and inbound details (replication from other groups to this group).
You should also monitor the usage of delegated space. If free delegated space is not available, replica reserve cannot increase
automatically.
Monitoring a Specic Replication Partner
You can monitor details about specic replication partners. For example:
• Partner name, IP address, and contact information
• Status of outbound and inbound replications between a partner and the group
• Details about inbound and outbound replicas and replica collections (for each partner)
• In-process replication activity between groups
• Amount of free delegated space
If free delegated space is low and the replica volume reserve for each replicated volume has not reached its maximum (and,
therefore, can increase), consider increasing the delegated space.
338
About Monitoring










